The Safety research team, empowered by the Safety malicious package detection technology, identified a threat actor publishing multiple malicious packages over the weekend. These malicious packages targeted the nx build system ecosystem.
tl;dr
In late August 2025, attackers exploited an insecure GitHub Actions workflow in the Nx build system to steal NPM tokens and publish malicious packages affecting over 15M weekly downloads. The attack occurred in two phases: first, malicious code harvested sensitive data from Mac/Linux machines and created public GitHub repos with stolen information; second, compromised GitHub tokens were used to make victims' private repos public. The incident impacted thousands of developers before containment, exposing critical open-source supply chain vulnerabilities.The background
Nx ecosystem was used to compromise developers
On August 26th, an attacker compromised eight NPM packages involving the Nx ecosystem. Nx is an AI powered build system for software engineering teams. The NPM packages involved are typically downloaded more than 15 million times a week.
You can read the officialGitHub security advisory for the incident HERE.
The attacker took advantage of a insecure GitHub Action workflow that had been published several days earlier. Security researcher Adnan Khan tweeted about the insecure PR when it was published, on August 22nd, but the development team didn’t understand the threat, so unfortunately a few days later on August 24th a malicious actor made a commit to the Nx GitHub project that allowed them to exfiltrate an NPM access token.
First Wave of the Attack
Two days later on August 26th, the threat actor started publishing malicious NPM packages using the stolen NPM token.
The following packages and versions were affected:
- nx (5.7M weekly downloads): - 21.5.0, 20.9.0, 20.10.0, 21.6.0, 20.11.0, 21.7.0, 21.8.0, 20.12.0
- @nx/devkit (4M weekly downloads): 21.5.0, 20.9.0
- @nx/enterprise-cloud (7k weekly downloads): 3.2.0
- @nx/eslint (1.7M weekly downloads): 21.5.0
- @nx/js (2.5M weekly downloads): 21.5.0, 20.9.0
- @nx/key (105k weekly downloads): 3.2.0
- @nx/node (651k weekly downloads): 21.5.0, 20.9.0
- @nx/workspace (2.5M weekly downloads): 21.5.0, 20.9.0
All of these packages are popular and together are downloaded more than 16 million times a week. The main, nx package is downloaded 5.7 million times a week.
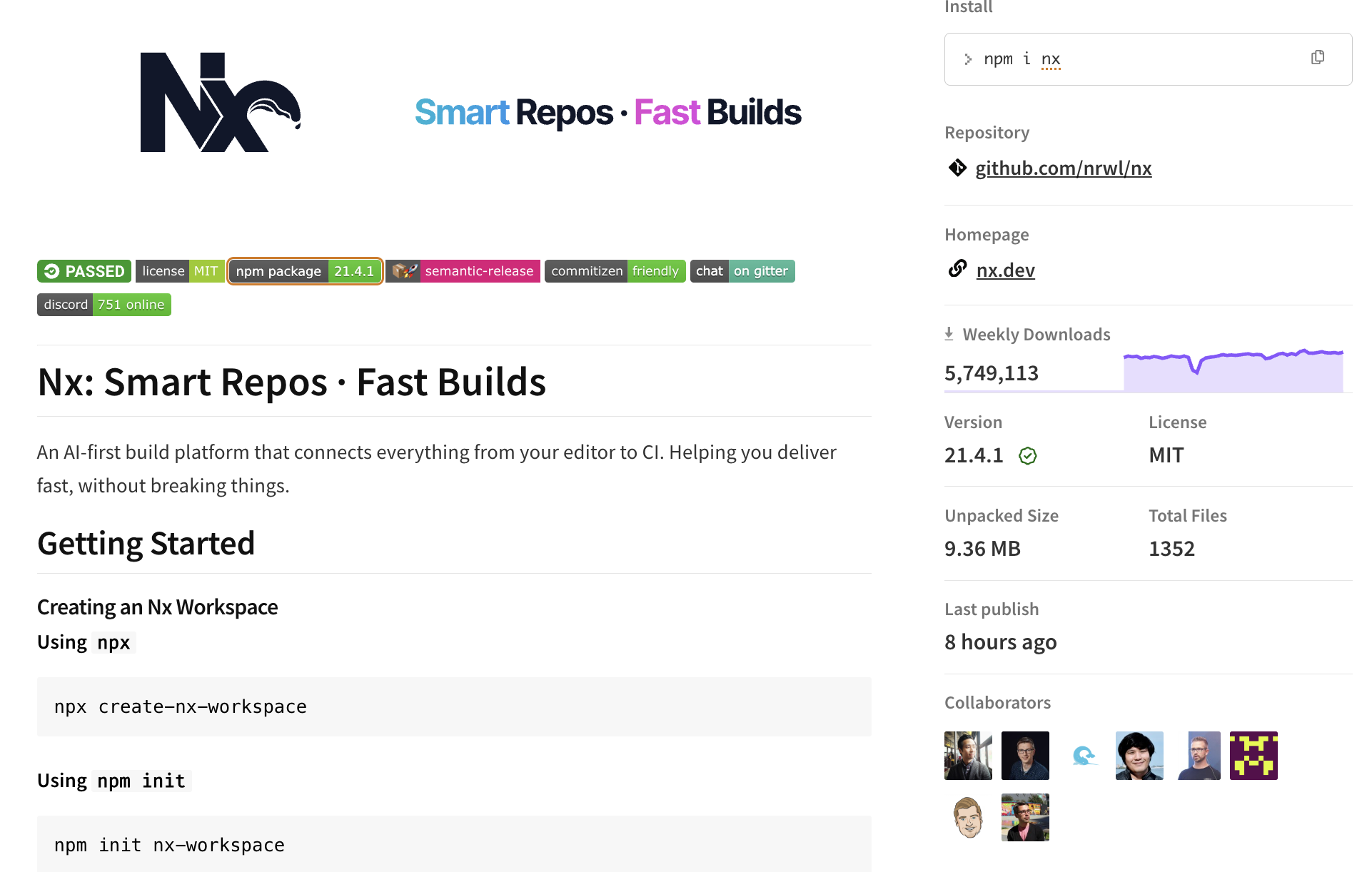
People take notice
The thing about attacking popular packages, is that people often notice changes in those packages as they try to use them. People started noticing pretty quickly that something was dodgy with the nx packages, and a GitHub issue was created.

The malicious versions of these packages were available on npmjs.com for about 4 hours before NPM removed them.
Nature of the Attack
The attack involved malicious code in the post-install script (telemetry.js) that executed automatically upon installation. There several interesting and unique things about this payload.
- Targeted Mac and Linux endpoints only (intentionally avoiding Windows). So refreshing to see Windows boxes left alone for once.
- Attempted to use locally installed AI tools to search for and identify sensitive files. The use of AI in this context seems almost as if it was a test, or proof of concept. The threat actor could have easily embedded a system command to search the filesystem for these files, but decided to use Gemini or Claude.
- Collected sensitive data including SSH keys, npm tokens, .gitconfig files, shell configurations, crypto wallets, and API keys for AI tools (Claude, Gemini, Q)
- Used a novel exfiltration technique - creating a public GitHub repository named "s1ngularity-repository" in the victim's own account and pushing the collected data there. Very smart to create an out of band exfiltration, but since the repos were public, pretty noisy.
- Added a "sudo shutdown -h 0" command to bash/zsh configuration files. Why? Possibly to hinder investigation, but again, seems unnecessarily noisy.
I talked to several people who were compromised in the attack who said they noticed changes to their .zshrc files or other local files changes. No one that I talked to disabled their GitHub or NPM keys however.
Second Wave of the Attack
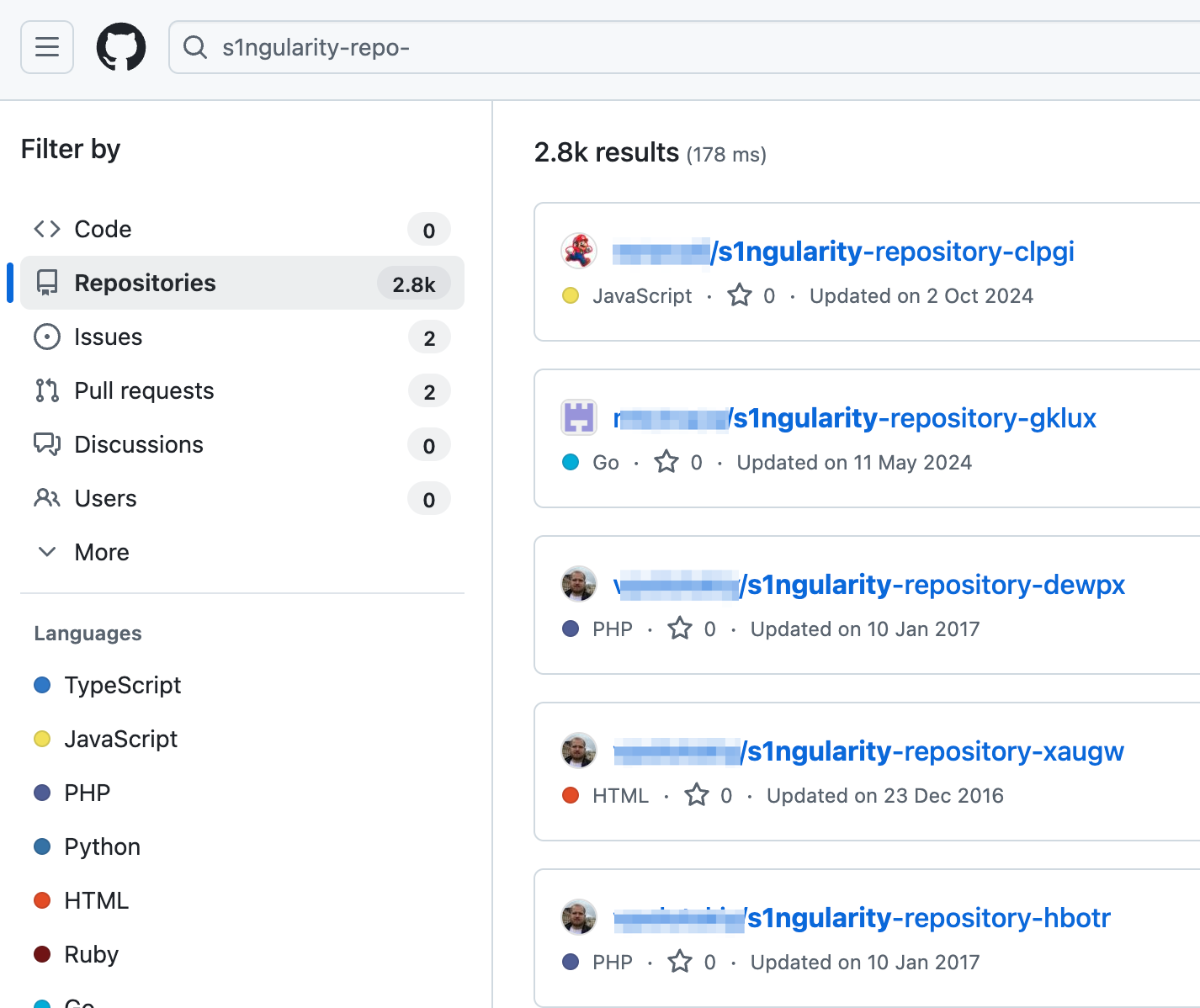
On August 28, a second wave of the attack was detected. GitHub tokens leaked in the initial compromise were being used to modify repositories in the compromised users GitHub account. The threat actors made private GitHub repositories public, exposing confidential data. If you searched GitHub for “s1ngularity-repo’*” you would see thousands of affected repos. In the screenshot below you can see that there were 2800 repositories in this search:
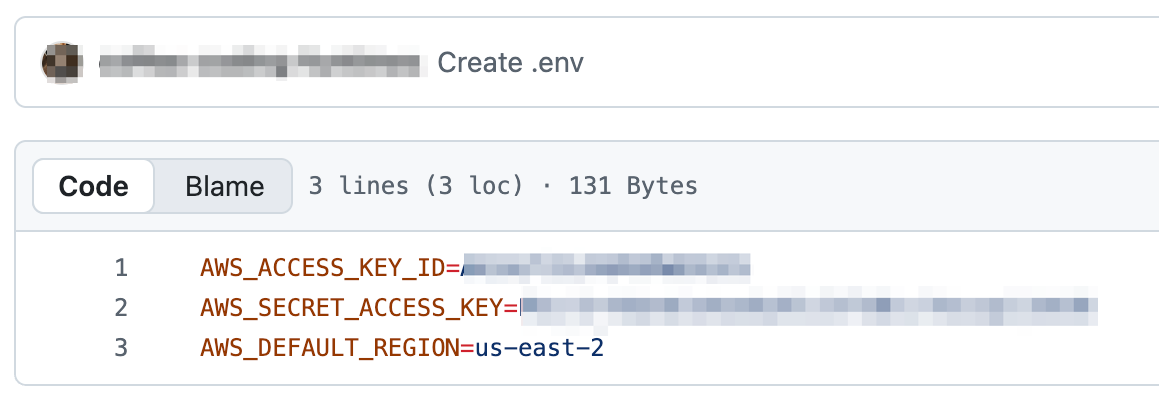
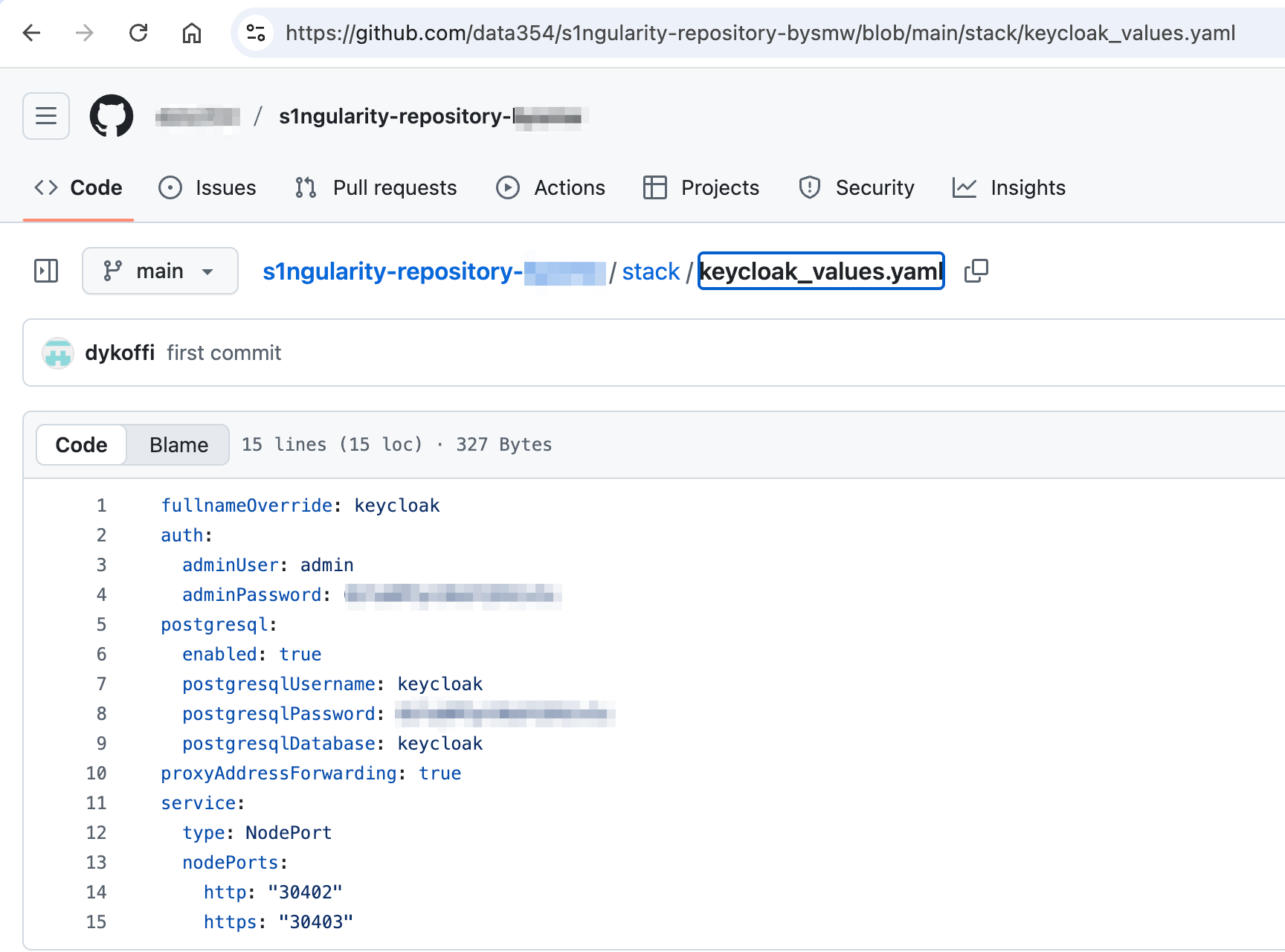
And if you examined some of those repositories you’d find sensitive data and credentials because the authors never expected those repositories to be public.
Serious impact
Over the course of three days I saw thousands of repositories with the name “s1ngularity-repository-xxxxx”. Most of the repos belonged to individual developers, but some of them belonged to companies, and I personally saw several universities affected.
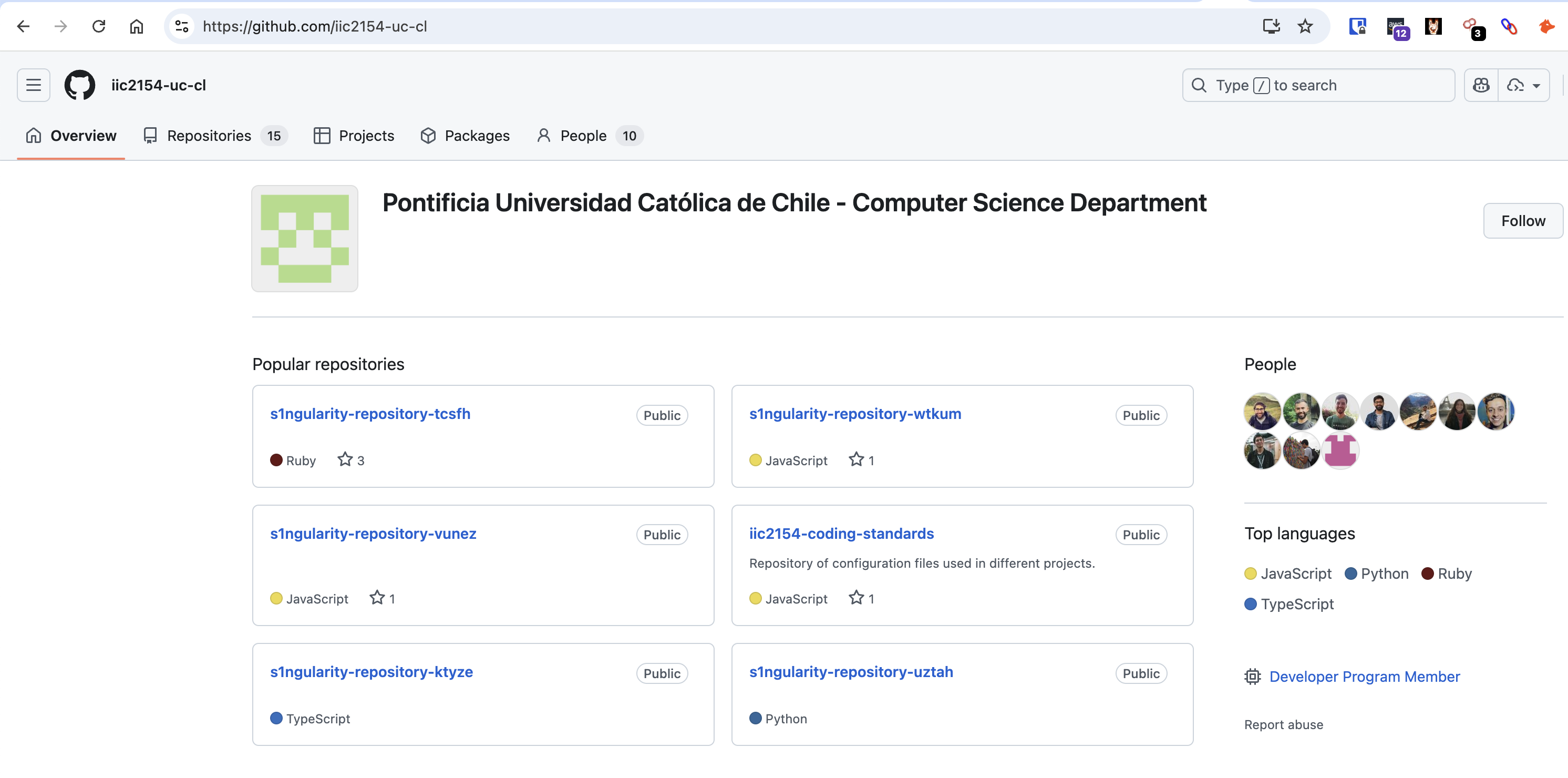
GitHub advised organizations to check for new repositories named "s1ngularity-repository-*" and initiate security incidents if found.
Here’s a timeline of important events
Initial Vulnerability (August 21-22, 2025)
- Aug 21, 4:31 PM: Vulnerability introduced via a PR with an insecure GitHub Actions workflow
- Aug 21, 10:48 PM: Security researcher Adnan Khan tweeted about the vulnerability
- Aug 22, 3:45 PM: Nx team attempted to revert the vulnerable workflow, but it remained accessible
Exploitation (August 24, 2025)
- Aug 24, 4:50 PM: Attacker made a commit that extracted the NPM token
- Aug 24, 5:04 PM: Malicious PR created triggering the vulnerable workflow
Attack Execution (August 26, 2025)
- Aug 26, 6:32-8:37 PM: Multiple malicious versions published across eight Nx packages
- Aug 26, 8:30 PM: First GitHub issue alerting about the compromise
- Aug 26, 10:44 PM: NPM removed affected versions and publishing capabilities
- Aug 26, 11:57 PM: All NPM tokens with publishing permissions revoked
Remediation (August 27, 2025)
- Aug 27, 1:53 AM: Security advisory published
- Aug 27, 3:33 AM: Team discovered VSCode extension (Nx Console) auto-installed malicious versions
- Aug 27, 8:33 AM: New version of Nx Console released without auto-install feature
- Aug 27, 11:57 AM: 2FA required for all Nx packages and moved to Trusted Publisher mechanism
- Aug 27, 3:28 PM: Additional restrictions added requiring team approval for external contributor pipelines
Second Wave of Attack (August 28, 2025)
- Aug 28, 8:00 PM: Threat actors began using GitHub access tokens stolen in the first wave of the attack to log into the compromised GitHub users accounts and make some of their private repositories public, and change the name of those repositories to “s1ngularity-repository-xxxxx”. This behaviour continued for roughly 48 hours with thousands of repositories suddenly made public. Any credentials, databases or other sensitive data in those repos was now publicly visible to anyone looking.
Remediating the Nx Supply Chain Attack
If you discover that you or your organization have been compromised by the Nx supply chain attack, follow these remediation steps immediately:
- Check for compromise: Use the indicators of compromise below to verify if you've installed any of the affected packages with the malicious versions
- Isolate affected systems: Disconnect compromised machines from networks to prevent lateral movement and data exfiltration
- Scan systems: Run comprehensive malware scans on all potentially affected systems
Technical Remediation
- Remove malicious packages: Delete the compromised Nx packages from your system
- Install clean versions: Reinstall with specific safe versions
- Disable Nx Console auto-updates: If using VSCode with Nx Console extension, update to the latest version that disables auto-install
- Rotate credentials: Change all potentially exposed credentials including:
- GitHub tokens and SSH keys
- NPM tokens
- Cloud service provider credentials
- CI/CD environment variables and secrets
- Audit for public repositories: Check if any private GitHub repositories were made public by the attack
- Audit Git history: Look for unauthorized commits that might contain malicious code
Security Enhancement
- Implement the Safety Firewall: The Safety Firewall wraps your package managers and stops npm from installing malicious packages. Safety Firewall works on your development machines AND in you CI/CD pipelines. You can read about Safety Firewall at https://docs.safetycli.com/safety-docs/firewall/introduction-to-safety-firewall
Indicators of Compromise (IOCs)
Based on my research this threat campaign has several IOCs you can look for:
NPM Packages:
- nx:- 21.5.0, 20.9.0, 20.10.0, 21.6.0, 20.11.0, 21.7.0, 21.8.0, 20.12.0
- @nx/devkit: 21.5.0, 20.9.0
- @nx/enterprise-cloud: 3.2.0
- @nx/eslint : 21.5.0
- @nx/js: 21.5.0, 20.9.0
- @nx/key: 3.2.0
- @nx/node: 21.5.0, 20.9.0
- @nx/workspace: 21.5.0, 20.9.0
Files
- 5a2168b679f6a1ac40893884c1271e23c3a7ea338a973ee46fcf76479f9cdd59 - ./telemetry.js
- 8eea1f65e468b515020e3e2854805f1ef5c611342fa23c4b31d8ed3374286a90 - ./telemetry.js
- 7ed5c47fe32d24f4925c24f661175f3676dca95a75e59e3f7e551944215f4de3 - ./telemetry.js
How can you protect your org from this kind of attack?
Existing security tools like SCA and EDR do not protect you from threats like the nx attack. Fortunately, there are ways to protect both your developers and CI/CD pipelines form attacks like this one.
The world's first AI-powered Software Supply Chain Firewall analyzes every package request in real-time, automatically blocking malicious and vulnerable dependencies before installation. Stop supply chain attacks at their source while maintaining development velocity.
Read more about our exciting Firewall product!
How can Safety help protect you from these attacks?
Traditional vulnerability scanning happens too late - after potentially malicious code is already in your system. Which means that ASPM and EDR solutions don't protect you from this type of threat.
But all is not lost, as the Safety Firewall protects develoeprs and CI pipelines proactively. Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.
You can sign up for a free Safety account and try the Safety Firewall HERE. Feel free to reach out to me with any questions!
Let us know if this blog post helped you
I hope this blog post has helped you. Feel free to hit me up directly if you have any questions about this campaign.

Paul McCarty - Head of Research, Safety
You can find me on LinkedIn and BlueSky.










