The Safety research team has identified an active credential phishing attack taking place on Wednesday, September 24th, 2025.
So far we've identified 120 packages that have been published by five
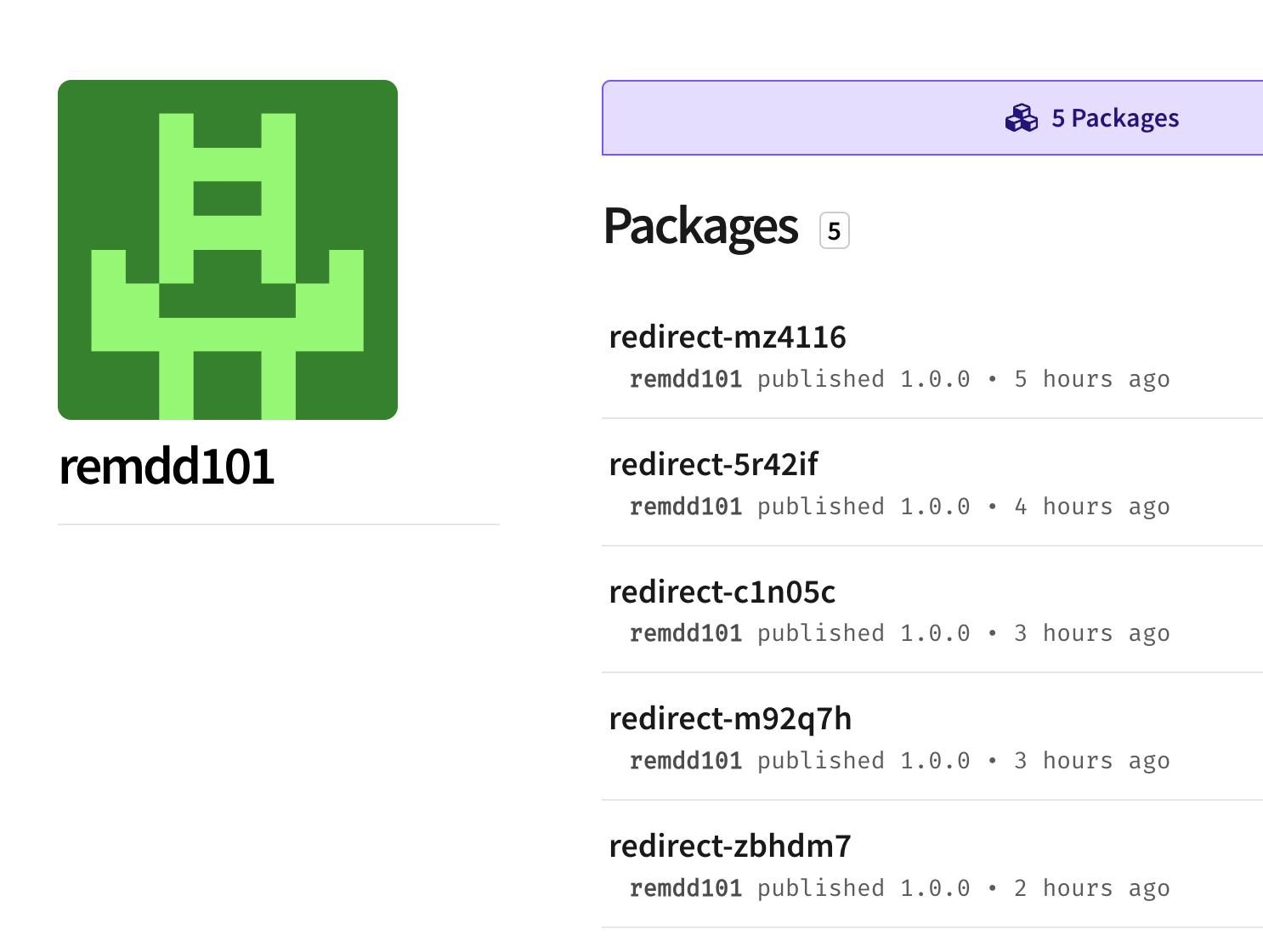
The packages are:redirect-5r42if
redirect-c1n05c
redirect-m92q7h
redirect-mz4116
redirect-zbhdm7
redirect-lxzc6c
redirect-qbzqro
redirect-ksm5w7
redirect-ystrj5
redirect-cn040w
redirect-f72kyw
redirect-xi84nq
redirect-24nt59
redirect-r0ajvl
redirect-fd91u6
redirect-j0rs4a
redirect-8ynd96
redirect-xs13nr
redirect-rrfeb9
redirect-9iak88
redirect-d0qfku
redirect-xgcv6j
redirect-t8kcsk
redirect-gjl674
redirect-5cxzgs
redirect-g7v030
redirect-04g1my
redirect-elvwba
redirect-7qnew0
redirect-gzkgcn
redirect-nron9d
redirect-shqv6v
redirect-vpvoos
redirect-hx522h
redirect-hi5ag9
redirect-95fl17
redirect-fohapy
redirect-5iqds5
redirect-0vaxnw
redirect-t09ul0
redirect-57j5wb
redirect-b9fv9e
redirect-cj50k2
redirect-uc8xfg
redirect-q2htwu
redirect-kz5pf4
redirect-n2wvec
redirect-406s9z
redirect-uxwcv8
redirect-e19jye
redirect-7yqujr
redirect-o92d2h
redirect-k4s26t
redirect-lbgja3
redirect-qx2www
redirect-n06xhl
redirect-zoju4g
redirect-j5blfb
redirect-b9diha
redirect-1hvx9g
redirect-u0e2q7
redirect-cx4vm0
redirect-ltlpoj
redirect-dna9sd
redirect-8py8qs
redirect-n95xyv
redirect-ubp4cs
redirect-sykre1
redirect-1ubpyu
redirect-evb9wa
redirect-q84l3v
redirect-594t6h
redirect-vlgk2c
redirect-fwx2y7
redirect-pqigpl
redirect-s7usff
redirect-1wc4gw
redirect-1st7z7
redirect-klea4q
redirect-x2giv7
redirect-k1jlsf
redirect-4r6ynv
redirect-ewce43
redirect-h4y8f0
redirect-za4566
redirect-47cprv
redirect-g7gn31
redirect-l6qi9e
redirect-4nwrkg
redirect-igk4sd
redirect-byj4f5
redirect-3viu68
redirect-mrdlde
redirect-e761hq
redirect-7vw41m
redirect-w9cx9u
redirect-r3s2jv
redirect-noyuan
redirect-63cl4f
redirect-qrah57
redirect-ht8x82
redirect-v74zee
redirect-a1gs61
redirect-dravb9
redirect-1akzwg
redirect-prhts6
redirect-k5j1u7
redirect-p8ris1
redirect-7bqfg6
redirect-y8p47m
redirect-1p89nj
redirect-g0ew1n
redirect-oroq43
redirect-6lvcjm
redirect-jw31kl
redirect-mz4116
redirect-5r42if
redirect-c1n05c
redirect-m92q7h
redirect-zbhdm7
redirect-uplctp
The redirect-mz4116 package that was published two hours ago:
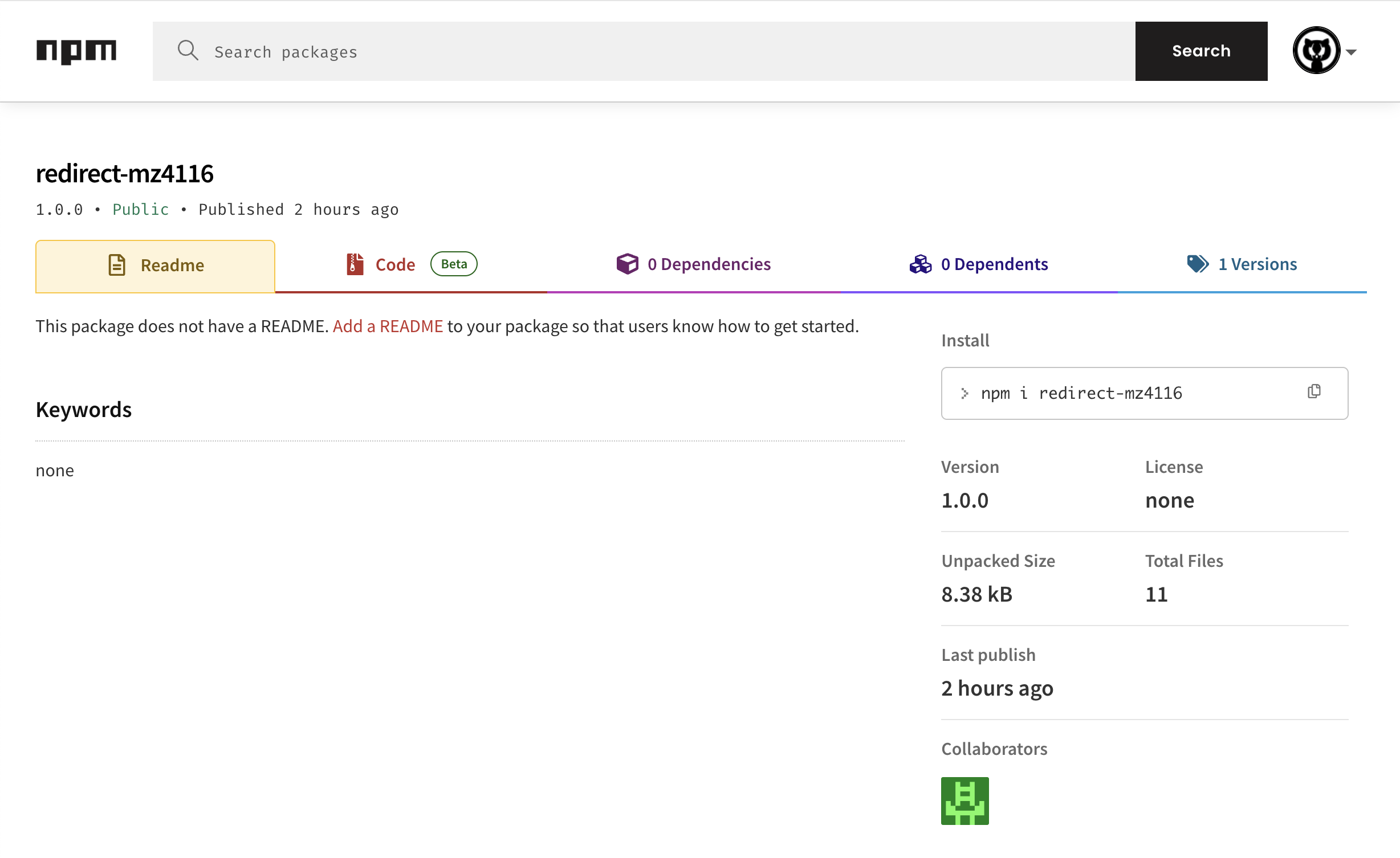
How the malware works:
The NPM packages come with a Python file called "redirect_generator.py":
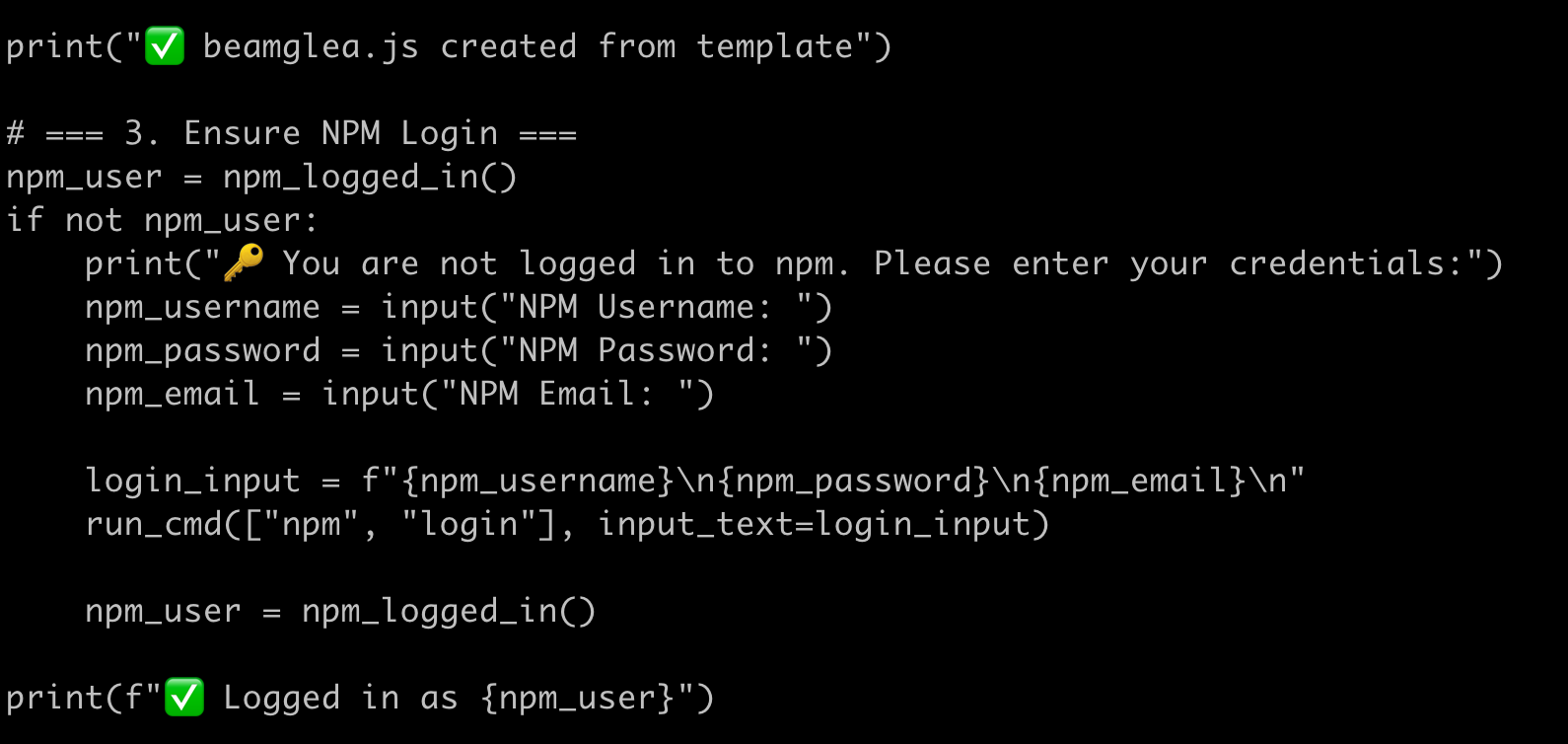
This python script takes three parameters:
1. A JavaScript template file, which is the beamglea.js file in this case.
2. An email address
3. A redirect URL
The python script then uses those three parameters to custom make a HTML page and an NPM package with the name "redirect-xxxxxx" where the x's are a random alphnumeric string. The python script injects the email address and custom HTML into the package. Once that package is live on NPM it can be served out via the UNPKG javascript CDN. The UNPKG links are clearly what the attacker wants to create and they are mentioned directly in the python and HTML files.
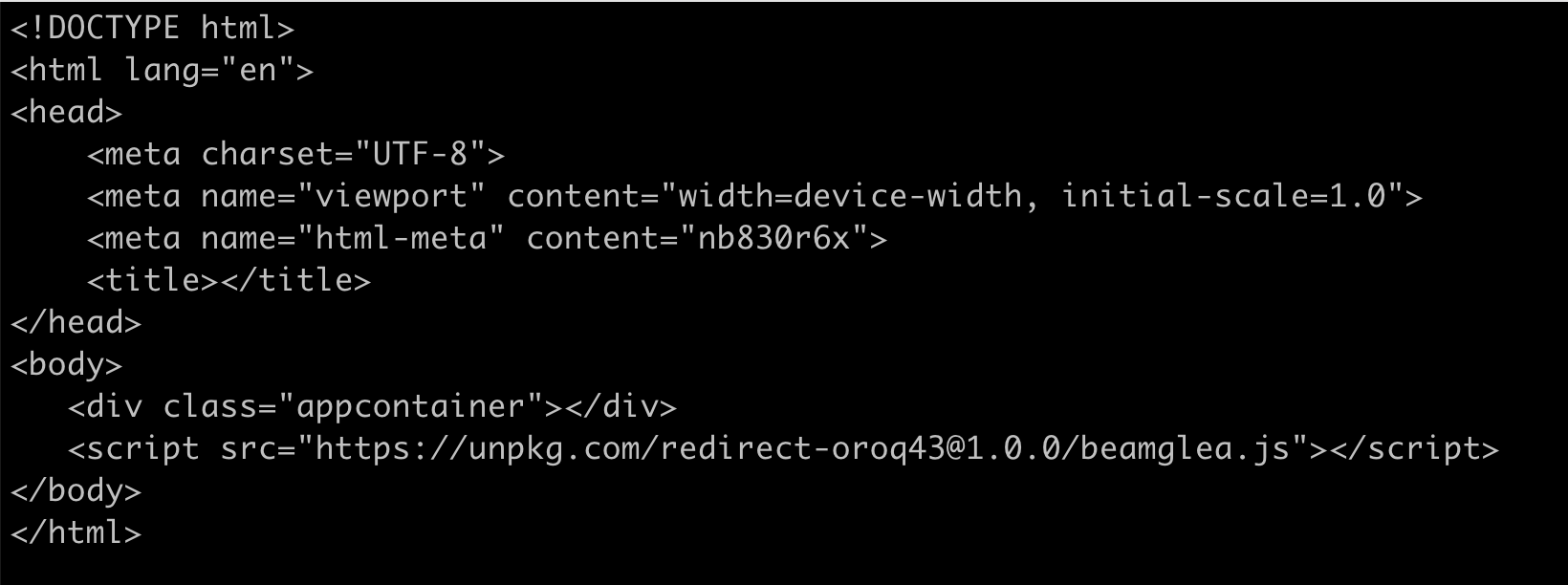
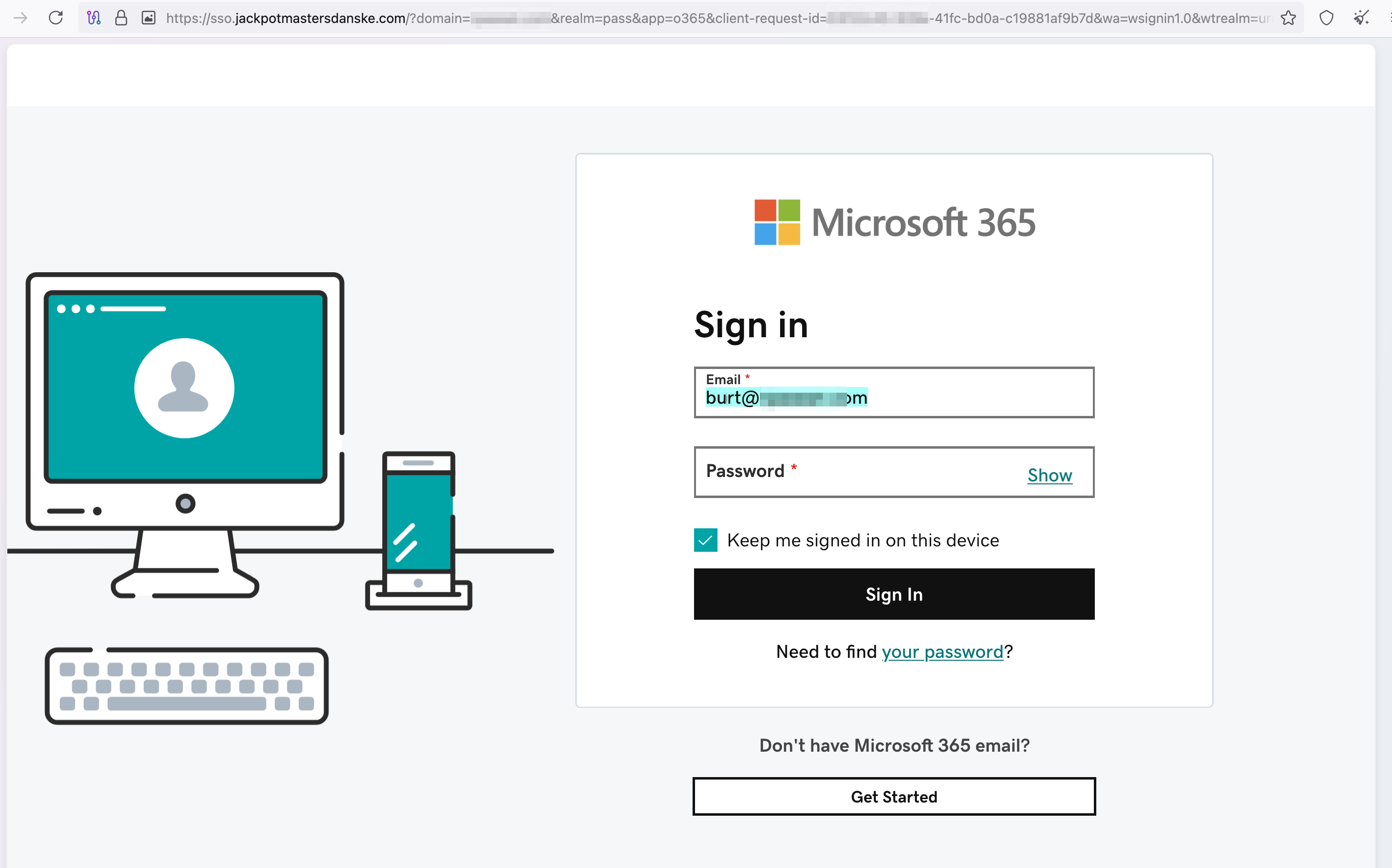
The phishing sites that are generated are pretty good for being created with such simple automation:
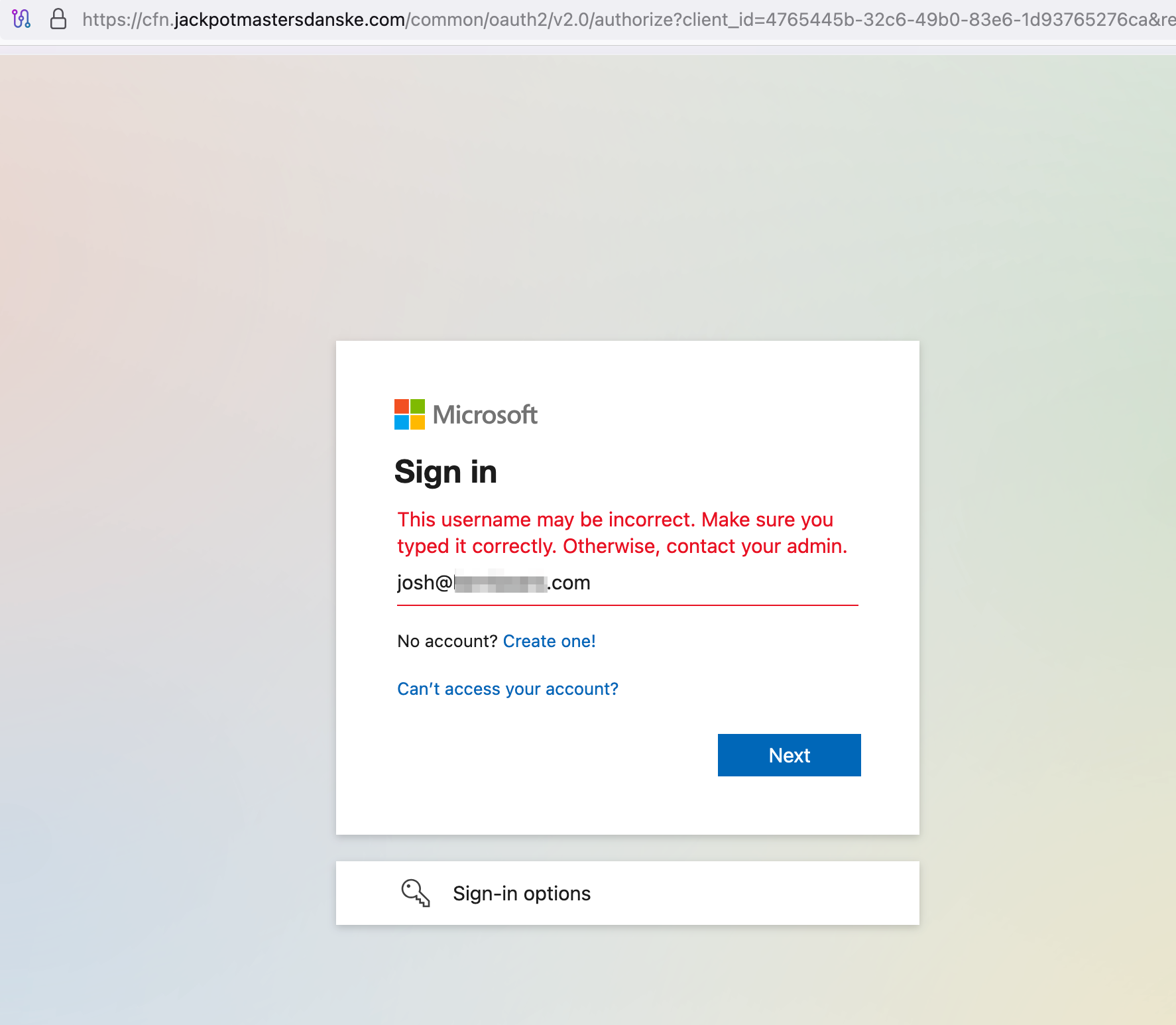
Each of these 0365 logins is customized for a specific employee at each of target companies.
Companies Targeted:
It appears as though specific companies are being targeted in the attack.
At this point we think that these companies are the intended victims of this attack, but we can't say for sure.
The intended victims:
Pinpoint Laser - pinpointlaser[.]com
Kern Laser - kernlasers[.]com
Roadpacker Asean - rpasean[.]com
Quadrise Energy- quadrise[.]com
Grant's Blinds - grantsblinds[.]com
AEGG - aegg[.]co[.]uk
CEJN - cejn[.]com
P81 - p81[.]co[.]uk
SaGiang - sagiang[.]com[.]vn
Hust - hust[.]hr
British SoftDrinks - britishsoftdrinks[.]com
United Well Medical Isotype - unitedwell[.]com
Saxtorp Trading - saxtorp[.]com
DEMAG - demagcranes[.]com
Innovation Rehab - innovationrehab[.]co[.]uk
Crouzet - crouzet[.]com
United Medical Products - unitedmedicalproducts[.]com
rgbelektronika.pl
buschvacuum.hu
fertilome.com
sasol.com
roshelop.co.il
orbitbid.com
camelgroup.it
sasol.com
fanyutools.com
integra-biosciences.com
redskylighting.com
chestermachinetools.com
jumbo-fasteners.com.tw
specialchem.com
Indicators of Compromise (IOCs)
Based on my research this threat campaign has several IOCs you can look for:
NPM Packages and Versions:
redirect-5r42if - 1.0.0 (all should be considered malicious)
redirect-c1n05c - 1.0.0 (all should be considered malicious)
redirect-m92q7h - 1.0.0 (all should be considered malicious)
redirect-mz4116 - 1.0.0 (all should be considered malicious)
redirect-zbhdm7 - 1.0.0 (all should be considered malicious)
URL/Domains:
jackpotmastersdanske[.]com
Our team is still gathering evidence and data and we will be reaching out to the affected companies in the next hour.
How can Safety help protect you from these attacks?
Traditional vulnerability scanning happens too late - after potentially malicious code is already in your system. Which means that ASPM and EDR solutions don't protect you from this type of threat.
But all is not lost, as the Safety Firewall protects develoeprs and CI pipelines proactively. Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.
You can sign up for a free Safety account and try the Safety Firewall HERE. Feel free to reach out to me with any questions!
Let us know if this blog post helped you
I hope this blog post has helped you. Feel free to hit me up directly if you have any questions about this campaign.

Paul McCarty - Head of Research, Safety
You can find me on LinkedIn and BlueSky.





.png)




